Cyber Kill Chain
1. Cyber Kill Chain 이란
Cyber Kill Chain은 군에서 사용하던 적의 활동을 식별하고 저지하는 단계별 접근 방식을 사이버 공격으로 해석한 개념으로 사이버 공격의 다양한 단계와 보안팀이 공격자를 탐지 및 차단할 수 있는 지점에 대해 설명한다.

2. Cyber Kill Chain 단계
- Reconnaissance(정찰)
공격 목표를 선정 및 분석하는 단계이다. 공격 목표가 선정되면 목표에 대한 정보를 수집한다.
웹 크롤링, 사회 공학 기법, 구인 공고의 기술 스택, 사용하는 백신 및 EDR , IP 대역 및 열린 Port 등 다양한 정보를 수집하여 앞으로 진행될 단계에 활용한다. - Weaponization(무기화)
초기 액세스에 사용될 악성코드가 개발되어 일부 유형의 익스플로잇 또는 전달 가능한 페이로드가 작성되는 단계이다. - Delivery(전달)
익스플로잇 또는 페이로드가 공격 목표에 전달되는 단계.
앞서 수집한 정보를 토대로 피싱, 스미싱, 악성 웹사이트로의 접속을 유도하여 무기화된 악성코드나 페이로드를 전달 하는 단계이다. - Exploit(익스플로잇)
전달된 악성코드, 페이로드가 트리거되는 단계이다. - Install(설치)
공격 목표에 악성코드가 설치되어 실행되는 단계이다. - C&C(명령 및 제어)
공격 목표에 설치된 악성코드가 C&C 서버를 통해 명령을 수행하고 공격 목표를 제어하는 단계이다. - Action(행동 개시)
내부 시스템의 기밀 정보 수집 및 시스템 파괴 등의 공격 수행 단계이다.
3. 단계별 탐지 및 대응 방안
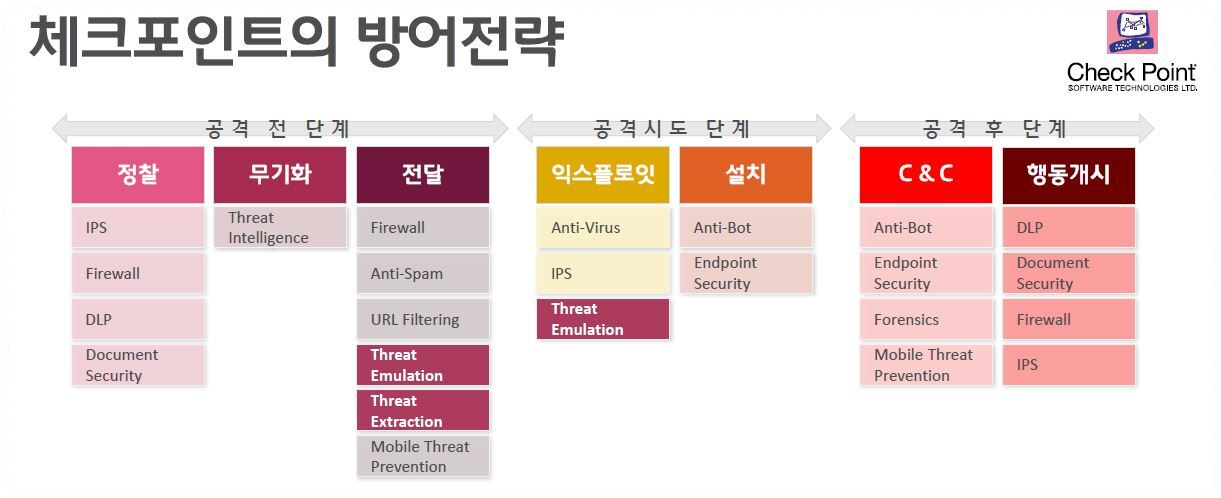

아래는 각 단계별 대응 방안이다.
| 단계 | 공격 방법 | 대응 방안 |
| Reconnaissance | - 이메일, 크롤링 - 사회공학기법 |
- IPS, FireWall, HoneyPot, Bastion Host |
| Weaponization | - 악성코드 및 페이로드 생성 - Trojan 등 결합 |
- IPS/IDS - Threat Intelligence |
| Delivery | - Drive By Download - Spear Phising |
- Anti Spam - URL Filtering |
| Exploitation | - 악성코드 및 페이로드 실행 - 취약점 이용 공격 |
- Endpoint Security(Anti Virus, HIDS) - PMS(3rd Party, OS Patch) |
| Installation | - Trojan, Backdoor설치| - Lateral Movement |
- Endpoint Security(Anti Virus, HIDS) - SIEM Monitoring |
| Commnad & Control | - 시스템 권한 획득 - 명령어 전달/제어 |
- IPS/IDS, FireWall - SIEM Monitoring |
| Actions | - 시스템 기밀 정보 수집 - 시스템 파괴 |
- DLP - IPS/IDS, FireWall |
참조
https://blog.skby.net/%EC%82%AC%EC%9D%B4%EB%B2%84-%ED%82%AC-%EC%B2%B4%EC%9D%B8-cyber-kill-chain/
사이버 킬 체인 (Cyber Kill Chain) > 도리의 디지털라이프
I. 사이버 공격 분석 모델, 사이버 킬 체인 가. 사이버 킬 체인의 개념 사이버 공격을 프로세스 기반 분석하여 각 단계 별 위협 요소 파악 및 공격 방법 정의 분석 모델 나. 사이버 킬 체인의 사상
blog.skby.net
https://www.itworld.co.kr/news/100774
ITWorld 용어풀이 | 사이버 킬 체인(Cyber Kill Chain)
사이버보안 세계에서는 뚫리지 않는 방패는 없다는 것이 이제 정설이 되었습니다. 공격자가 충분한 시간과 자원을 갖고 꾸준히 공격한다면 뚫지 못할
www.itworld.co.kr
사이버킬체인(Cyber Kill Chain)모델을 통한 SIEM의 활용
이글루시큐리티 PS팀 황범석 부장(bumseokjr@igloosec.com) 최근 북한이 6차 핵실험을 단행함에 따라 사드, ICBM등의 군사 용어가 뉴스나 포털 사이트 실시간 검색을 통해 많이 알려지고 있다. 사
www.igloo.co.kr
https://www.crowdstrike.com/cybersecurity-101/cyber-kill-chain/
What is the Cyber Kill Chain? Introduction Guide - CrowdStrike
The cyber kill chain is an adaptation of the military’s kill chain, a step-by-step approach that identifies and stops enemy activity. Learn more here!
www.crowdstrike.com
'🪬Incident Respose' 카테고리의 다른 글
| Threat Modelling (0) | 2023.12.06 |
|---|---|
| STRIDE Framework (0) | 2023.11.23 |
| 보안 동향 참고 사이트 (0) | 2023.10.15 |
| MITRE ATT&CK (0) | 2023.08.20 |
댓글
이 글 공유하기
다른 글
-
Threat Modelling
Threat Modelling
2023.12.06 -
STRIDE Framework
STRIDE Framework
2023.11.23 -
보안 동향 참고 사이트
보안 동향 참고 사이트
2023.10.15 -
MITRE ATT&CK
MITRE ATT&CK
2023.08.20